Cyber threats and suspicious network activities continue to evolve, driving the expansion of global regulatory requirements. These circumstances address overall security challenges and reshape how businesses must approach data protection through particular security measures. We all know that in the face of such dynamic changes, cybersecurity is no longer a "nice to have" addition when it comes to integration configurations - it’s an absolute “must to have”. For enterprise teams managing sensitive data exchange in projects, tasks, service requests, incident tickets, and other valuable information across tools like Jira, ServiceNow, Azure DevOps, and others, the integration layer must be airtight for seamless business operations.
At Getint, we are aware that for many of our clients - especially those from finance, healthcare, or IT sector, who need to comply with industry standards - asking “Is this integration platform secure enough?” isn’t just a good question. It’s a mandatory one. And it’s our responsibility to give you a clear, confident, and well-documented “yes.”
In this article, we review all the cybersecurity standards that Getint has achieved so far, exploring the crucial certifications and best practices we follow on a daily basis to protect your data storage - so you can integrate with peace of mind.
Security Built-In, Not Bolted-On
Let's start by introducing some of our fundamental security measures. From the beginning, security has been embedded into the foundation of how Getint is built and operated - whether we are talking about SaaS or On-Premise version. It’s not something we slap on after the fact - it’s part of our culture, in which three key areas: confidentiality, integrity, and availability persist in the play. This commitment is reflected in how we design our systems, how we handle your data, how we train our team, and how we continually improve our existing systems.
On-Premise deployment: full behind-the-firewall capability
Offering an On-Premise solution, we allow it to operate entirely behind our customers' firewall - integrated within the company's infrastructure to provide an additional layer of both security and control.
And even though the customer uses cloud solutions like Jira Cloud, ServiceNow Cloud, DevOps Cloud they can use Getint as an On-Premise tool. The same option goes with migrations between systems. Our solution lets you migrate from tool to tool via On-Prem versions.
SaaS deployment: encryption in transit & encryption in rest
According to the best standards supported by all the platforms we integrate, in our SaaS environment, we use SSL encryption with HTTPS to protect data as it moves between systems.
Encryption for storing and transmitting sensitive data is crucial for cybersecurity reasons. This is why we applied this method of protection to all keys and secrets, which are securely stored on servers that we own. Specific details about key management practices are withheld to maintain security.
Data storage
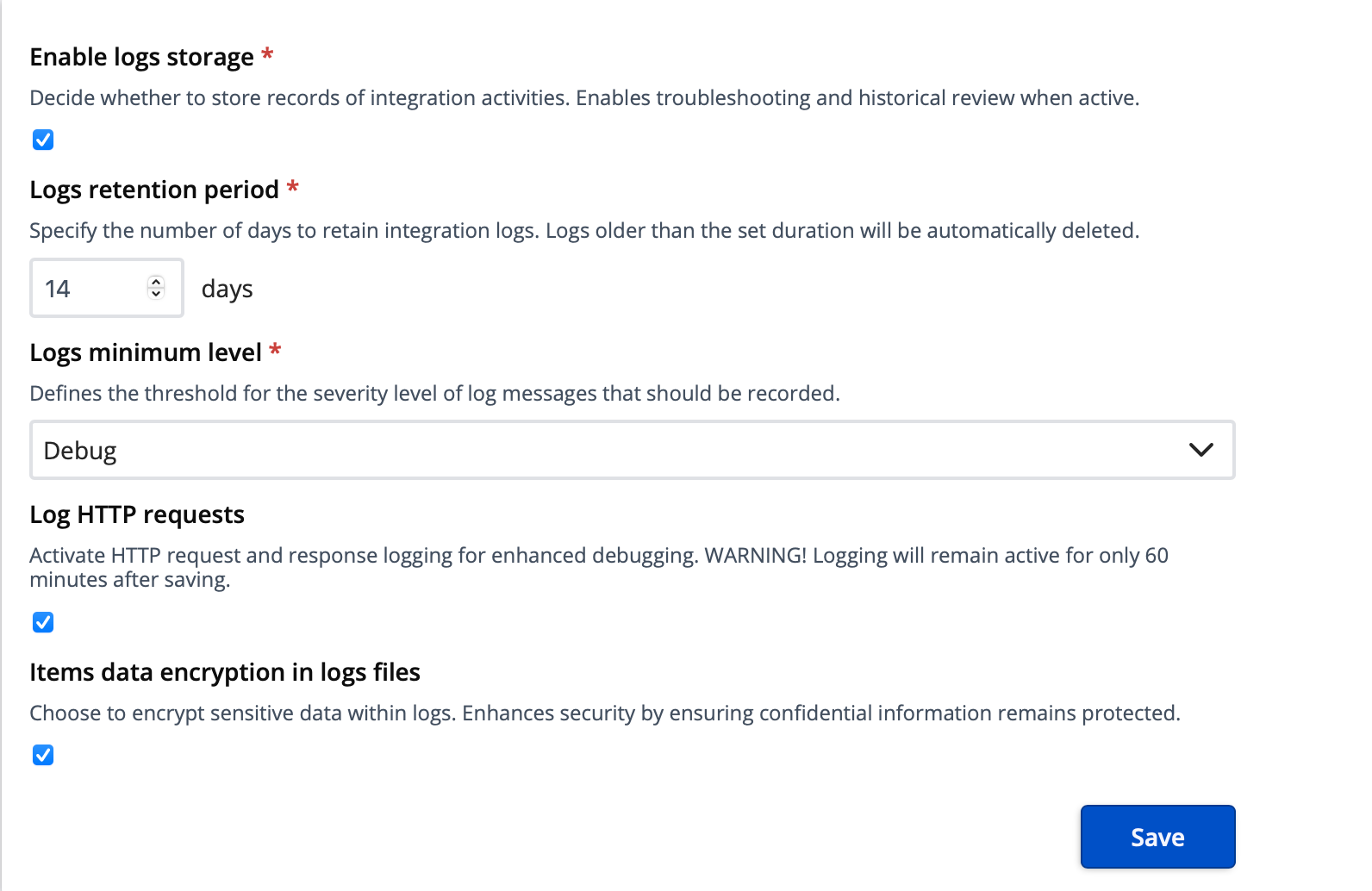
Data is stored on the cloud (AWS), utilizing HTTPS for encryption in transit and it’s up to you how long the logs should be stored - by default it’s 14 days but you can also turn off the option of storing or set it for only a day.
Also, within the data storage platform settings, you can enable Logs Encryption to ensure all integrated field values are protected.
Reporting
Thanks to the logs, Getint provides highly advanced options for issues tracking, enabling users to maintain oversight of their integrations, respond to issues proactively, and continually optimize performance.
This robust feature supports the integrity and security of synchronization operations across all the platforms.
With reporting capabilities you can:
- monitor sync frequency and system health
- identify performance trends and pinpointing slow or inefficient processes (users managing multiple integrations can assess a status of each run)
- ensure accurate and complete data transfer across systems
- recognize early detection and resolution of operational failures
- identify items that failed to sync and get to know why
- confirm expected job execution and adjust or stop jobs when necessary
MFA for internal systems
- Authentication is enforced with strong password policies and frequent rotation.
- Access to internal systems used by Getint company members is enforced by multi-factor (MFA) authentication.
Data residency
We are committed to helping companies align their data storage practices with operational needs. The standard option for data residency is a shared tenant located in the EU or USA, but by the fact we operate on AWS, we also have the enterprise option to set up a dedicated tenant in a location chosen by the customer - along with shorter synchronization intervals.
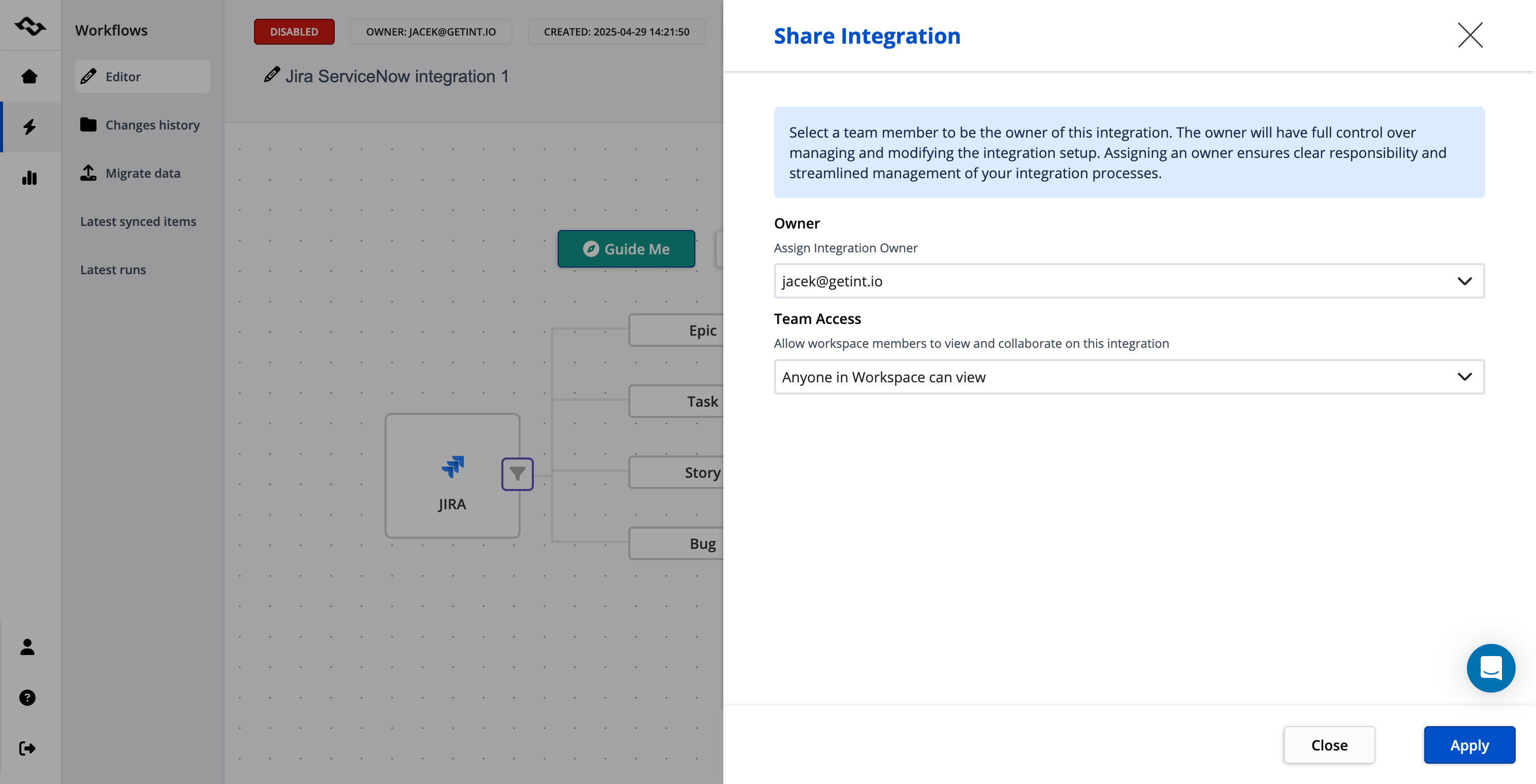
Role-based access control
You can set access to Getint integrations and connections based on the two levels:
- Only Jira admin can log in, configure settings, and give permissions to other Jira users - by creating a particular group and giving them credentials. There is an option for SSO (Single Sign-On).
- The second option is sharing access in the Getint application itself - you can set what is the level of access, whether others can only view or edit.
Integration Partner - Not Just an Out-of-the-Box Tool: Proxy, Custom API’s, Custom Development
When you choose Getint, you’re not just getting a ready-made integration tool. You’re gaining a partner committed to your success. Our experience working with enterprise customers proves that we're ready to go beyond standard features to meet your unique technical and security requirements.
Whether it’s adding support for proxy environments, working with custom APIs, or building entirely new connectors, our team is here to deliver tailored solutions that fit your organization.
- In collaboration with Raiffeisen-Landesbank Steiermark and ByteSource, we developed proxy support to comply with strict security requirements - Jira Data Center to Jira Cloud integration;
- For multiple enterprise customers using our Jira-ServiceNow integration, we enabled compatibility with MuleSoft and custom ServiceNow APIs.
- For one of the biggest automotive brands, we implemented a custom scripting feature to extend their integration flexibility - Azure DevOps to Jira Data Center migration.
- With Airbus Protect, we built an entirely new connector tailored to their specific platform needs - Jira to ServiceNow integration.
"In the difficulties integrating our customer ticketing tools with our own, Getint is a partner of choice. Its seamless integration capabilities are what we were looking for." - Deian Vikov, Project Lead at Airbus Protect.
These cases highlight how we operate not as just a tool provider that has restricted capabilities, but as a true integration Partner that can adapt to your requirements.
Explore more case-studies.
Atlassian Jira Security Systems
When discussing secure integrations, it's worth mentioning Jira software access control policies. Atlassian employs a comprehensive security framework to protect Jira and its integrations, ensuring that both administrators and users can operate with confidence.
Robust authentication with JWT
Atlassian Connect apps authenticate using JSON Web Tokens (JWT). During the installation process, a security context is exchanged between the app and the Atlassian host product, containing an installation secret. This secret is used to create and validate JWT tokens for API calls. Such a method guarantees that only authorized applications can interact with Jira, preventing unauthorized access and potential data breaches.
Secure communication with HTTPS
All communications between Jira and its integrations are encrypted using HTTPS. This encryption ensures that data transmitted over the network is secure from interception and tampering. Additionally, Jira enforces the use of TLS version 1.2 or higher, along with HTTP Strict Transport Security (HSTS), to further safeguard data in transit.
Comprehensive security requirements for Connect Apps
Atlassian has established strong security requirements for Connect apps listed on the Atlassian Marketplace.
- Authentication and authorization
Ensuring that all endpoints are authenticated and authorized, with JWT or OAuth 2.0 validation for every request - Getint uses tokens or OAuth authentication mechanisms to connect directly to the apps where applicable.
Example: Using Jira admin - to create a connection you provide URL, email, and token.
- Data protection
Implementing full disk encryption at rest for any Atlassian end-user data stored outside of Atlassian products.
- Application security
Maintaining secure domains, implementing security headers, and regularly updating third-party libraries to mitigate vulnerabilities.
By adhering to these requirements, Atlassian ensures that integrations with Jira maintain a high standard of security, protecting both user data and system integrity.
Let’s now take a closer look at Getint certifications which are also an important security layer.
GDPR & CCPA Compliance: Privacy by Design
With customers across the EU and beyond - California, GDPR and CCPA legibility isn’t optional for us, it’s essential. At Getint, that means putting user privacy first in every integration we build. We’re careful with data collection, applying data minimization by default - gathering only what’s necessary to make our service work smoothly. Nothing more, nothing hidden.
We’re upfront about where data is stored, how it's protected, and what rights customers have under GDPR and CCPA - including access, correction, and deletion of their data. Every enterprise customer relationship starts with a clear Data Processing Agreement, outlining exactly how personal data is handled.
Through these practices, we embed privacy into the design and deployment of every integration.
SOC 2 Type II: The Standard of Trust
Integrations security means that we constantly grow. Our SOC 2 Type II certification marks a milestone in our ongoing effort to meet - and exceed - enterprise-grade security posture.
We partnered with Vanta, a leading compliance automation platform, and completed a third-party audit independently proceeded by Prescient Security that confirmed our controls meet the rigorous standards set by the AICPA Trust Services Criteria:
- Security - your integrated systems and data flows are protected from unauthorized access and data loss or breach.
- Availability - your sensitive information and systems are accessible as intended.
- Confidentiality - confidential information is treated as such.
- Processing integrity - data processing is complete, correct, precise, and prompt.
- Privacy - your data is secured. As a customer you are informed about the way of collection, use retention, and disposal of data.
SOC 2 Type II evaluates how we operated over time, and it reflects our day-to-day reality.
“Achieving SOC 2 means our platform is ready to support the most security-conscious customers in the world. But more importantly, it confirms we’re walking the talk - not just preparing for audits, but operating at this level every day.”
Jacek Wizmur-Szymczak, Co-Founder at Getint
Want to read our certification journey in more details? Skip to our article: Getint Achieved the SOC 2 Type II Certification via Vanta.

ISO 27001: Information Security, Formalized
Before SOC 2, we had already prepared security foundations by adopting the ISO 27001 framework - the international gold standard for managing information security, playing a critical role in integration security.
It's not also just another policy document on a shelf. With ISO 27001, we’ve implemented a company-wide Information Security Management System (ISMS) that covers everything from secure software development to incident response. We’ve built a systematic approach to identify potential vulnerabilities, implement controls, mitigate risks and improve these actions continuously - it's important to not react only when something goes wrong. The ISO 27001 certification gives us a structured way to think about security systems across the entire company, from onboarding new users to managing third-party vendors.

ISO 27018: Personal Data in the Cloud
As for a company providing cloud integration solutions, protecting personally identifiable information (PII) is especially important. That’s why, to support this, we’ve adopted ISO 27018, a privacy-focused extension of ISO 27001 that sets guidelines specifically for handling personal data in cloud environments. This includes:
- Robust encryption policies
- Transparent data handling and retention procedures
- Third-party processor compliance
- Timely breach notification protocols
- Internal privacy training and audits
Together, ISO 27001 and ISO 27018 create a powerful framework for managing sensitive data security and privacy in complex integration ecosystems.

Beyond Certifications: Active Vigilance
Our integrations’ security doesn't end with certificates on the wall though.
We actively maintain Atlassian’s Cloud Fortified status - a badge earned through rigorous security, reliability, and support reviews only to Marketplace partners that meet criteria of providing secure integrations. Cloud Fortified apps undergo advanced screening, uptime guarantees, and operational readiness assessments. It ensures our product is resilient, monitored, and tested under real-world usage.
We also operate an active Bug Bounty Program via Bugcrowd - trusted hackers and security researchers test our platform for vulnerabilities. Every report is handled responsibly and addressed swiftly, enabling us to stay one step ahead of security threats that traditional testing might miss. Our internal security posture is also continuously monitored by Vanta, which ensures controls are enforced and keeps us ready for audits or legibility checks at any time.

And as a Platinum Partner on the Atlassian Marketplace, our platform has already passed rigorous technical and compliance reviews from one of the most security-conscious ecosystems in the world.
What This Means for You As a Customer
For you - whether you’re in IT, compliance, legal, or operations - our cybersecurity approach means fewer roadblocks, faster onboarding, and stronger peace of mind.
- For security teams, it reduces friction during procurement and provides evidence of strong, independently verified security controls.
- For legal teams, it means clearly documented DPAs, privacy rights, and transparency.
- For enterprise buyers, it accelerates due diligence cycles - and helps meet internal and regulatory requirements, improving overall efficiency.
Most importantly, when you integrate tools with Getint, you're not just connecting platforms. You're choosing a partner with proven security credentials, operational transparency, and a security culture that never stops evolving.
Whether you’re syncing Jira with Azure DevOps, managing incidents between ServiceNow and Jira Service Management, or aligning DevOps and ITSM pipelines, your data deserves enterprise-grade protection at every layer.
Use Case: Secure API Integration Between Jira and ServiceNow
Let’s consider a real-world scenario. An enterprise customer needs to integrate Jira (used by their development team) with ServiceNow (used by their IT service management team) to streamline incident handling and change management workflows.
To enable this, Getint connects to both platforms via respective Application Programming Interfaces (APIs) - allowing near real-time data flow between the two systems. This raises several critical questions for the customer’s security and IT compliance teams:
- How are API keys stored and protected?
- What happens if a key is exposed or compromised?
- Can access be scoped and revoked?
- Is data encrypted during the API call and at rest?
Here’s how Getint answers these integration security challenges:
- API key protection - all API keys used to access Jira, ServiceNow, or other tools are stored using AES encryption and securely isolated per integration instance. They are never exposed in plaintext, either in logs or UI.
- Least Privilege Access - we enforce scoped API permissions, meaning keys only have access to the exact data fields and endpoints needed for the integration to function - nothing more.
- Key rotation & revocation - keys can be rotated at any time, and integrations can be immediately disabled through the UI or automated control panels.
- Data security in transit - all API communication is secured via SSL, ensuring data is encrypted end-to-end between Getint and your platforms.
Security As a Journey: Summary
At Getint, we don’t see security as a finish line - it’s a continuous journey of vigilance, improvement, and accountability. Certifications like GDPR, SOC 2 Type II, ISO 27001, and ISO 27018 are essential milestones, but real trust is built through day-to-day practices, transparent operations, and proactive defense.
By combining security certifications with Cloud Fortified validation, and an open-door Bug Bounty Program, we ensure that our integrations remain not only functional and scalable but also fundamentally secure.

























